Introduction
In an era where data breaches are increasingly common, safeguarding sensitive
company data has become a top priority for organizations. Traditional security methods
often need to catch up in protecting against sophisticated cyber-attacks, necessitating a
more robust and dynamic approach. This is where Zero Trust Network Access (ZTNA)
comes into play. By operating on the principle of never trust, always verify, ZTNA
ensures that every user and device accessing the network is continuously authenticated
and authorized, providing more data protection.
The frequency and sophistication of cyber-attacks are rising, with cybercriminals
employing advanced tactics to infiltrate networks and steal sensitive data. In response,
organizations must adopt proactive measures to secure their digital assets and stay
ahead of potential threats. ZTNA addresses these challenges by implementing stringent
security protocols that adapt to dynamic business environments. By doing so, it not only
protects sensitive data but also bolsters an organization’s overall cybersecurity posture.
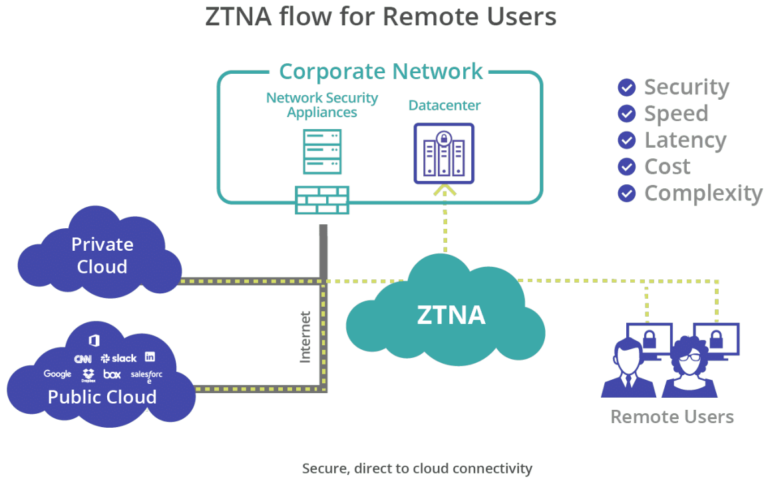
How ZTNA Works in Data Protection
ZTNA secures sensitive data by verifying users identities and their devices compliance
with them before granting access to network resources. ZTNA performs stringent
checks upon every access attempt, including user credentials, device health, and behavioral analysis. This multi-factor authentication approach significantly reduces the
risk of unauthorized access and data breaches.
Understanding what is ZTNA involves recognizing its layered security measures. ZTNA
creates trust zones within the network, ensuring that even if cyber intruders gain entry,
they cannot move laterally to access sensitive data. Continuous monitoring and
adaptive policies further enhance security, making it difficult for unauthorized users to
exploit network vulnerabilities. This approach contrasts sharply with traditional
perimeter-based security models, which often leave significant gaps in protection once
the perimeter is breached.
ZTNA’s approach is efficient in environments where devices and users frequently
change, such as remote work setups and Bring Your Device (BYOD) policies. By
consistently verifying each access request, ZTNA can swiftly identify and respond to
potential threats. This dynamic security model is essential for maintaining robust
defenses in today’s fast-paced and ever-evolving digital landscape.
Benefits of ZTNA for Sensitive Data
Enhanced Security: ZTNA’s continuous verification process ensures that every
access request is legitimate, minimizing the chances of unauthorized data access.
This zero-trust approach significantly reduces the attack surface, making it harder
for cybercriminals to breach the network. By validating every connection attempt,
ZTNA eliminates implicit trust, a primary weakness in traditional security models.
1 Efficient Access Management: ZTNA offers granular access controls, allowing
organizations to define who can access the data under which conditions. This
precise access management ensures that sensitive information is only available to
authorized personnel. These controls can be tailored to specific roles and
responsibilities, ensuring that employees only access the data necessary for their
tasks, thus minimizing the risk of internal threats.
2 Compliance with Regulations: Many industries are subject to strict data
protection regulations. ZTNA helps organizations comply with these regulations by
ensuring that access to sensitive data is continually monitored and controlled. This
safeguards data and protects businesses from potential legal and financial
repercussions. By maintaining detailed logs of access attempts and enforcing
stringent security measures, ZTNA simplifies the process of regulatory compliance
and audits.
3 Scalability and Flexibility: ZTNA can be easily integrated with cloud services,
allowing businesses of all sizes to scale their security infrastructure as needed.
This flexibility ensures that its security measures can grow as an organization
grows without compromising protection. ZTNA’s adaptability makes it a viable long-
term solution capable of evolving alongside technological advancements and
business expansion.
Reducing Insider Threats
Whether malicious or accidental, insider threats pose a significant risk to sensitive
company data. ZTNA mitigates these threats by continuously monitoring user behavior
and device compliance. Any deviation from established norms triggers an alert,
prompting immediate action to prevent potential data breaches. By employing
behavioral analytics and anomaly detection, ZTNA can swiftly identify suspicious
activities and respond accordingly.
ZTNA also enforces strict access controls that limit employees access to only the data
and resources necessary for their roles. This principle of least privilege further reduces
the risk of insider threats by ensuring that users cannot access sensitive information
beyond their authorization. Regular security training and awareness programs can
complement ZTNA by educating employees about best practices and the importance of
adhering to security protocols.
Limiting the Impact of Potential Breaches
Even in the unfortunate event of a network breach, ZTNA limits the potential damage.
By compartmentalizing network access, ZTNA ensures that intruders cannot move
laterally to access other network parts. This containment approach minimizes
the impact of a breach, protecting sensitive data from wide-scale exposure. By isolating
compromised segments, ZTNA prevents the spread of malicious activities across the
network.
Implementing ZTNA in Your Organization
Implementing ZTNA involves several critical steps to ensure a seamless transition and
optimal protection of sensitive data. The process starts with evaluating your security
infrastructure to identify gaps and assess where ZTNA can enhance safety. Next,
selecting a reliable ZTNA solution provider is crucial. The provider should offer
comprehensive services aligning with your organization’s needs and security goals.
The next step is to integrate ZTNA with existing systems and applications. This involves
detailed planning and testing to ensure compatibility and minimize disruptions.
Employee training is essential to ensure the workforce understands the new security
protocols and their roles in maintaining data integrity. Effective training programs should
cover the basics of ZTNA, its benefits, and how employees can contribute to
maintaining a secure digital environment.
Continuous monitoring and assessment are vital to maintaining the effectiveness of the
ZTNA framework. Automated solutions for real-time tracking and updates are
recommended to stay ahead of emerging threats. Regular reviews and updates of
security policies based on monitoring outcomes help refine and strengthen the ZTNA
deployment. Establishing a dedicated security team to oversee ZTNA operations can
ensure that the system remains effective and adapts to evolving threats and business
needs.
Conclusion
The role of Zero Trust Network Access (ZTNA) in protecting sensitive company data
cannot be overstated. By continuously verifying users and devices, ZTNA provides a
robust security framework that significantly reduces the risk of data breaches. Its
granular access controls, compliance support, and scalability make it an indispensable
tool for modern organizations aiming to safeguard their valuable data assets.
With cyberattacks becoming increasingly sophisticated, adopting a zero-trust approach
to network security is not just a best practice but a necessity. Implementing ZTNA
equips businesses with the tools to protect sensitive information, ensure regulatory
compliance, and maintain stakeholder trust. By doing so, companies can focus on
growth and innovation, knowing their critical data is secure.